
IT Incident Management (Image by callcare247)

IT Incident Management (Image by callcare247)
IT incident management is a crucial facet of Information Technology Service Management (ITSM), but it’s not the same.
So, ITSM is like the whole kit and caboodle of IT services – it’s the big picture. But when we zoom in, we find IT incident management.
This IT incident management is where the action happens when things go a bit haywire in your IT services.
IT incident management is about jumping into action and fixing those unexpected glitches. While ITSM encompasses the entire spectrum of delivering IT services.
But, the significance of IT incident management cannot be overstated. Even a small IT issue can cause significant operational and financial setbacks. Therefore, a strong incident response process is an absolute necessity.
Effective IT incident management involves identifying the root cause of incidents, resolving them quickly, and implementing measures to prevent similar problems from occurring in the future.
This proactive approach is crucial to maintaining the stability and reliability of IT systems, which in turn supports continuous business operations.
This discussion will delve into IT incident management in greater detail. The goal is to provide you with a fundamental understanding of how to run IT Incident Management to meet your business needs.
IT Incident Management (ITIM) is the organized response to unplanned events affecting IT services. It prioritizes, tracks, and resolves incidents to minimize business disruption and restore service as quickly as possible.
The whole idea is to get things back on track as fast as possible, with as little disruption to your business as possible.
So, what is the secret behind ITIM? First off, it’s all about being systematic. It’s a well-thought-out process that’s part of the bigger picture of IT service delivery.
The steps are pretty clear: spot the problem, figure out what’s causing it, and fix it pronto. Speed is of the essence here because the less downtime, the better. The big goal? To make sure your business keeps running smoothly.
Yes, ITIM is there to ensure that your IT services meet the standards you’ve promised your customers, by quickly resolving incidents and keeping those dreaded disruptions to a minimum.
But ITIM isn’t just a quick fix; it’s also about looking at the bigger picture. After sorting out an issue, it digs deeper to find out why it happened in the first place.
IT incident management and risk management are closely interconnected processes that are essential for maintaining a secure and efficient IT environment.
Risk management focuses on identifying, assessing, and mitigating potential risks, which helps in preventing IT incidents.
When incidents do occur, IT incident management steps in to respond effectively, drawing on the insights gained from risk assessments.
That’s why we have a detailed article that focuses on the risk management process. Check out the article to learn how the risk management process supports IT incident management.
This way, ITIM not just fixes problems, but also prevents them from happening again. ITIM is a continuous cycle of improvement, always fine-tuning the process to make sure your IT support is top-notch and your business runs without a hitch.
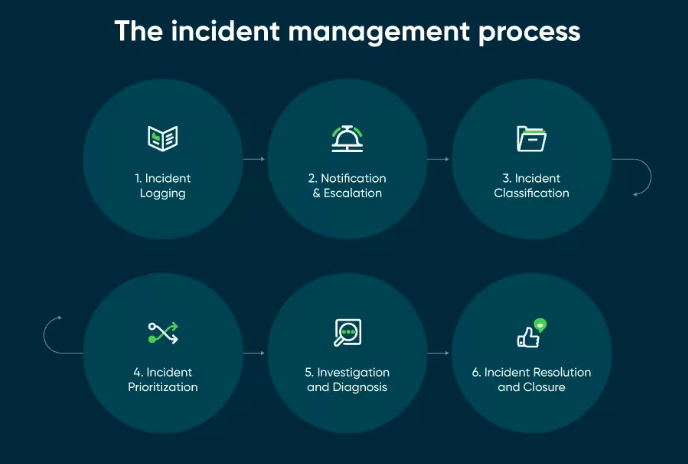
Navigating through IT Incident Management is like being part of an IT relay race, where every leg of the journey is vital and seamlessly connects to the next. Let’s dive into each stage:
The journey begins when someone notices something’s off, or your trusty automated systems flag an issue.
This moment is crucial – it’s when the incident is given an identity, a ticket that captures all the important details: what’s up, who’s affected, and what it might mean for the business.
In order to address the issue at hand, you need to utilize a combination of tools. Firstly, implementing a ticketing system such as Microsoft Service Desk (which is part of Azure Active Directory).
Secondly, utilizing automated monitors like AWS CloudWatch Agent. Finally, it is important to also consider the human aspect of the situation and rely on the observations of your users.
Once we know what we’re dealing with, it’s time to sort out these incidents. It’s a bit like triage – figuring out which issues are the heavy-hitters that need immediate attention and which can wait a bit.
Are they biggies that can cause chaos or smaller hiccups? This sorting, or categorizing, helps decide which fire to put out first. The big, disruptive ones are top of the list.
You can use prioritization matrices and your SLAs (Service Level Agreements) as guides to make these calls.
Now, the right IT minds take charge, focusing on keeping the issue from escalating. It’s a bit like putting a safety net around the problem – isolating it, finding quick fixes, and making sure it doesn’t get worse.
At this stage, incident response tools, like CrowdStrike Falcon, and swift communication are key.
This is the step where a serious investigation takes place. The IT team investigates by analyzing data, logs, and user feedback to identify the root cause. Understanding the cause of an incident is crucial in resolving it.
We rely on diagnostic software and logs, such as Microsoft Azure Monitor, and frequently collaborate across teams to gain broader insights.
Once you cracked the code and figured out the root cause of the IT issue, the next crucial step is to take action and set things right.
This stage is all about moving from understanding the problem to actively solving it. This stage could involve various actions depending on the nature of the problem.
Therefore, the solutions range from patch management tools to hardware fixes, depending on the need.
For patch management, Cisco SecureX Patch can be used as a tool. You can use AWS CloudTrail for diagnostic and configuration tools. Alternatively, Microsoft Azure Arc for servers can be utilized to address hardware issues.
After successfully navigating through the turbulence of an IT incident and restoring normal service, it’s time for one of the most crucial steps in the process: closing the incident and documenting everything that happened.
This phase is not just a formality, but also a valuable learning opportunity and a foundation for future improvement.
You can use a ticketing system, such as Microsoft Service Desk, and incident reporting and analysis tools, such as Microsoft Defender for Cloud, to improve your documentation and learning center workflow.
To maximize the effectiveness of these tools, it is important that they are properly integrated and used to integrate and be documented.
Post-incident review and analysis are essential for growth and improvement in IT Incident Management. This phase converts individual incidents into learning opportunities, promoting a proactive approach to process improvement.
By reflecting on actions and outcomes, you can address current challenges and fortify your business for future scenarios.
This step concludes the incident management cycle and sets the stage for continuous development and refinement of your IT practices.
For tools and methodologies, you can streamline review meetings and incident analysis tools to aid in the analysis and understanding of each response.
Each step in IT incident management, from the initial alert to the final review, is an important piece in the process of keeping your IT services resilient and reliable.
And, please remember that you are not limited to the tools and methodologies listed above. These tools and methodologies can be expanded and adapted as needed to meet the needs of the organization.
Let’s take a closer look at the best practices for effectively managing IT incidents. It’s all about being clear, prepared, and smart with your resources.
Setting the scene and staying ahead in IT incident management is about clear definitions, well-defined roles, smart use of automation, and a proactive stance. How?
First of all, what exactly is an IT incident? This is where you need some clear guidelines. Having well-defined criteria helps ensure that everyone’s on the same page, leading to a quick and consistent response.
This means when something goes wrong, there’s no scratching heads wondering if it’s an incident or not.
Then, there’s the matter of knowing who’s in charge of what. So, when an incident strikes, everyone is ready to jump into action without any confusion. It streamlines the process and makes sure the right people are handling the right tasks.
And don’t forget about automation, your ever-ready helper. From logging incidents to sending out the first round of notifications, automation handles these tasks efficiently.
This automation process frees up your team’s time so they can focus on more complex issues that require a human touch.
Also, think about being proactive rather than reactive. Instead of waiting for issues to blow up, you use advanced monitoring tools and threat intelligence to spot potential problems early.
When you’re dealing with IT incidents, the way you handle them really counts. It’s not just about jumping into action quickly; it’s about a whole strategy that ensures you’re not just putting out fires, but also strengthening your IT framework for the future.
The first thing you need is a game plan to figure out which ones to tackle first. This is where your prioritization system comes into play.
It’s crucial to know which incidents are the heavy hitters – the ones that can cause the most disruption or damage.
The next step is to keep everyone in the loop. From your IT team to your broader stakeholders, everyone should know what’s happening as it happens.
This kind of open communication is important. It builds trust, alleviates concerns, and ensures that everyone understands the situation.
Okay, next, assemble a group of experts, each with his or her own superpower, to solve a problem. By encouraging your teams to work together and share their diverse skills and knowledge, you will find solutions faster and more effectively.
After dealing with an incident, take a step back and ask: Why did this happen? Root cause analysis is about digging deeper than the surface problem.
Understanding the underlying factors that led to the problem will help you and your team. In this way, you can prevent similar incidents from happening in the future.
And yes, don’t let any incident pass by without learning from it. Document everything – what happened, how it was tackled, and the key takeaways.
Each incident teaches you something and contributes to a knowledge base that’s invaluable for future incident management.
Continuous improvement at ITIM is about being proactive, learning, and always striving to improve your strategies and capabilities.
What’s more, it’s a commitment to never stop growing and adapting. That way, your IT infrastructure is not only solid today, but also prepared for tomorrow.
This continuous improvement means regularly analyzing incident data and user feedback to identify areas for improvement in your ITIM process.
Always remember, this data-driven approach ensures you’re not just guessing; you’re making decisions based on solid facts.
Then, make sure you have post-incident reviews. These sessions are invaluable; they help identify the root causes and the systemic issues.
Continuous improvement also means regular training and development for your IT team.
Your IT players need to be equipped with the latest tools and tactics, and prepared for evolving threats and more complex scenarios.
No matter what new challenges arise, investing in your team’s skills means you’ll always be ready.
Then, always make sure there are drills and simulations. This stage is your team’s rehearsal for the real thing. Conducting them regularly is like having scrimmage practices before the big tournament.
This phase will boost your team’s confidence and help you identify any gaps in your response plan. When a real incident occurs, your team will already know what to do, making your response smoother and more effective.
Making your IT infrastructure more resilient is a continuous and interrelated process, with each phase reinforcing the next to create a seamless, stable defensive infrastructure that’s ready for anything.
Let’s take a look at how you can make your IT infrastructure not just resilient, but practically bulletproof.
The foundation of a resilient IT system begins with robust backup systems and disaster recovery plans. This first phase sets the framework by making sure that there’s a recovery plan in place.
Once the foundation is laid, strong security measures act as the solid foundation of your defenses. This stage is directly related to your disaster recovery plans.
Yes, good security means reducing the chances that those disaster recovery plans will need to be activated. After all, good security prevents breaches in the first place.
The next phase is the proactive maintenance of your fortress walls – patching and managing vulnerabilities. This is a crucial link between setting up your defenses (security measures) and being ready for emergencies (disaster recovery).
Regular maintenance and updates ensure that the security measures stay effective, minimizing the chances of a disaster that would require deploying your recovery plans.
Finally, ensuring that your disaster recovery plans are always updated completes the cycle of resilience.
This phase is interconnected with all previous phases – your backup systems need to be ready to take over if security measures fail, and regular patching ensures that recovery plans account for the latest threats.
IT incident management is a dynamic and ongoing journey to embrace change and advanced technology.
This means staying on top of the changing environment and leveraging powerful technologies to expand your capabilities.
You can be prepared for what’s coming by keeping an eye on emerging technology trends and threats.
This approach will help you build incident management practices that are not just reactive to today’s challenges, but are designed for the future.
Next, think of AI and automation as the powerful engines that propel your ship forward. AI tools can predict incidents, analyze data, and even respond automatically, which is crucial in speeding up resolutions.
Yes, utilizing AI and automation can help you stay ahead of the curve by providing the agility and speed to quickly adapt to new trends and threats.
Finally, the right tools can make a significant difference in how effectively your team manages incidents.
This phase is intertwined with leveraging AI and automation – as you embrace these advanced technologies, the tools you choose will either amplify their benefits or limit their potential.
Reflecting on our discussion about IT incident management, it’s clear that having a strong and efficient approach is crucial for any business in today’s tech-driven environment.
So, if you’re looking to bolster your business’s IT capabilities, focusing on enhancing your IT incident management is a wise move.
Investing in maintaining current operations and preparing for future technological challenges is important because in the dynamic world of IT, being proactive and adaptable isn’t just an advantage-it’s a necessity.