
IT Incident Management Process (Image by Intellect QMS Software)

IT Incident Management Process (Image by Intellect QMS Software)
An effective incident management process is fundamental to ensuring smooth operations and business continuity across all industries.
This structured process involves the identification, handling and resolution of unforeseen incidents. Its importance lies in its ability to minimize disruptions.
A structured incident management process provides several benefits. Yes, incident management reduces response times, mitigates risk, and ensures compliance.
This helps protect an organization’s reputation, minimizes operational disruptions, and results in cost savings.
Incident management process is a collaborative approach to minimizing the impact of unplanned events on the delivery of services or products by restoring normal service operation as quickly as possible and learning from the event to prevent future occurrences.
Consider a sudden hiccup disrupts your online orders, a power outage shuts down your factory, or a data breach puts customer information at risk.
These unexpected incidents can disrupt your business and consume valuable time and resources.
That’s where incident management comes in as your vigilant protector. Its primary goal? To quickly identify, address, and resolve incidents before they escalate.
Or, you can simply refer to the incident management process as an early warning system for your business.
Because, the incident management process is constantly scanning for problems and triggering a rapid response to restore normal operations.
Whether it’s a server failure, a shipping delay, or a data breach, incident management provides you with a strategy to minimize damage, restore operations, and gain valuable insights to prevent future disruptions.
Problem management and incident management are distinct yet interconnected processes within IT and business frameworks, focusing on addressing and resolving different aspects of system disruptions.
IT incident management, the more immediate of the two, centers on quickly addressing and resolving incidents – unplanned disruptions or reductions in service quality – to restore normal service operation as swiftly as possible.
This process is designed to minimize the impact on business operations and maintain service availability.
This process involves identifying, logging, categorizing, prioritizing, and resolving incidents.
If an incident is too complex, it gets escalated for more specialized attention. The primary goal here is to limit the negative impact on business activities and users, ensuring a rapid return to normalcy.
In contrast, problem management takes a longer-term approach. It focuses on identifying, analyzing, and eliminating the root causes of incidents.
This process involves a deeper investigation to prevent recurrence of similar incidents.
While incident management is reactive, problem management is proactive, aiming to improve overall service quality by addressing underlying issues that might not be immediately apparent during an incident.
Both processes are central to effective IT service management, with incident management providing immediate relief and problem management ensuring long-term stability.
Together, they enhance overall service quality and reliability, supporting seamless business operations.
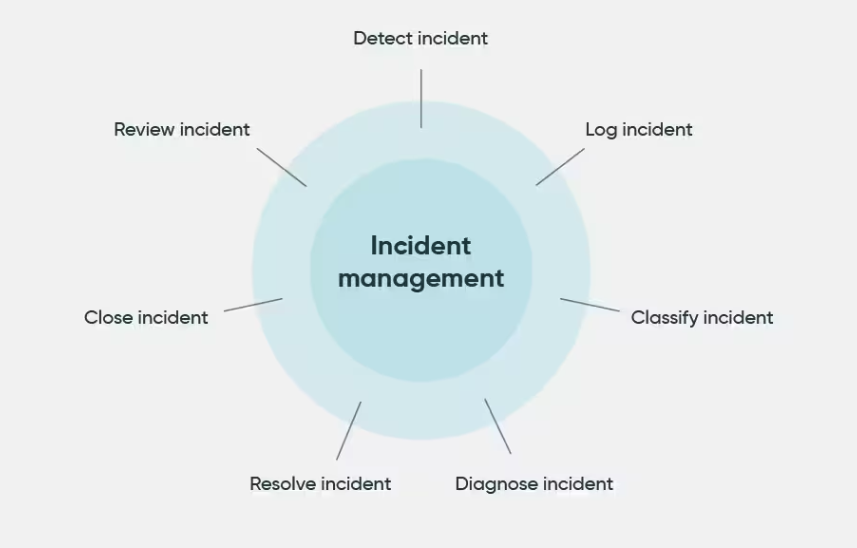
The incident management process, integral to IT and business operations, comprises a structured workflow designed to effectively handle and resolve incidents. This workflow is characterized by several distinct stages.
The process begins with identification, the critical first step where an incident, an unplanned interruption or reduction in quality of IT services, is detected.
This process could be through automated alerts or user reports. Once identified, the incident must be logged.
The logging stage involves recording essential details about the incident, creating a documented record that is crucial for tracking and management purposes.
Following logging, the incident undergoes categorization, where it is classified based on its nature and impact.
This stage helps in organizing incidents into manageable groups for more efficient handling.
Subsequently, the incident is prioritized based on factors like impact on business operations and severity, ensuring that resources are allocated to the most critical incidents first.
Investigation is the next crucial phase, involving a detailed analysis to understand the incident’s cause and find a solution. This stage is pivotal for developing an effective resolution strategy.
Resolution, as the term implies, involves implementing a fix to address the incident, aiming to restore normal service operation as quickly as possible.
The final stage is closure, where, after ensuring the incident is fully resolved and normal service is restored, the incident is formally closed, and documentation is updated to reflect the resolution process.
The whole structured approach in the incident management process is essential for swift and efficient resolution of IT service disruptions, thereby minimizing impact on business operations.
A robust incident management process hinges on three fundamental components: people, processes, and technology.
People are the cornerstone; they encompass the IT staff, support teams, and decision-makers responsible for responding to and resolving incidents.
Their roles, responsibilities, and communication channels must be well-defined to ensure effective collaboration and swift action.
Processes form the framework guiding these responses. This process involves established procedures for incident identification, logging, categorization, prioritization, response, and resolution.
These procedures must be clear, consistent, and adaptable to various incident types.
Lastly, technology underpins the entire process. This includes tools for incident detection, tracking systems for logging and monitoring progress, and communication platforms for coordination among team members.
These technological solutions should be reliable, user-friendly, and integrated seamlessly into the business’s IT infrastructure.
Together, these components create a cohesive system that enables efficient and effective resolution of incidents, minimizing disruption to business operations.
Incident management thrives on swift action and clear decisions. While processes provide the framework, it’s the tactical details inside that really turn the tide. Here are some pointed tips for improving your incident response.
When it comes to incident management, preparation and planning are non-negotiable. And, please note, a well-documented incident response plan is absolutely vital.
This plan should outline specific procedures, roles, and communication protocols to ensure clarity and efficiency during an incident.
Equally important is the role of regular training and exercises for response teams. These exercises not only familiarize personnel with the plan, but also help identify potential weaknesses.
Regular training ensures that teams not only know the procedures, but are able to execute them under pressure, greatly improving the effectiveness of the incident management process.
We need to recognize that clear and timely communication during incidents is not only beneficial, it’s essential.
The immediacy of conveying critical information to relevant stakeholders can significantly impact the resolution time and the overall disruption caused.
Simultaneously, establishing predefined communication protocols and channels is essential.
Designating a specific team or individual to communicate ensures consistent and authoritative updates.
Meanwhile, using multiple platforms-email, instant messaging, and internal communication systems-ensures broad reach.
And regular updates, even when there is no progress, help manage stakeholder expectations and maintain trust.
This structured approach to communication underpins a successful incident management strategy and improves overall response and efficiency.
The integration of technology into the incident management process is a major step forward.
Advanced incident management tools enhance efficiency by automating key tasks like incident detection and logging.
This automation accelerates response times, reducing the potential impact of incidents.
Additionally, these IT incident management tools facilitate better tracking and analysis, aiding in a more structured response.
They also ensure accurate documentation and provide valuable data for post-incident reviews.
The strategic use of technology, therefore, not only streamlines the incident management process but also improves its overall effectiveness.
Continuous improvement is the embodiment of an iterative approach. At the same time, we also see post-incident reviews providing insight into what worked and what didn’t.
This retrospective analysis is crucial for identifying both strengths and areas needing improvement.
Feedback loops are equally important, allowing for the incorporation of lessons learned into the process.
This iterative refinement ensures that each incident not only resolves the immediate issue but also enhances the overall incident management strategy, promoting a cycle of continuous learning and improvement.
Incident management in different industries showcases the versatility and critical nature of the process. Here are three real-world examples.
Back in 2018, Marriott International found themselves in a serious fix. Picture this: over half a billion guest records, just gone.
Hackers got their hands on everything – names, passport numbers, email addresses, and even details from the loyalty program.
So, Marriott didn’t waste any time, detecting the breach within days and immediately looping in the authorities and those affected.
They didn’t just hide behind corporate speak; they were upfront about it, issuing public apologies and keeping everyone in the loop about what they were doing to fix things.
They even set up a special website and call center to handle all the questions and concerns from guests.
Marriott knew they needed the big guns to tackle this, so they brought in top-notch cybersecurity experts to dive deep into the breach.
Compliance was key, too. Marriott Internationa stayed in lockstep with data protection authorities, ticking all the boxes when it came to reporting requirements and regulatory concerns.
the 2021 Colonial Pipeline incident wasn’t a small-scale intrusion; it was an assault on the largest fuel pipeline operator in the U.S., causing a shutdown that reverberated through the fuel supply chain to the East Coast.
This crisis led to gas shortages and soaring prices, sparking widespread public anxiety.
The handling of this situation by Colonial Pipeline is a subject of debate and scrutiny.
Colonial Pipeline acted swiftly, shutting down systems to block further infiltration.
Bringing in cybersecurity experts was a decisive move, demonstrating their commitment to containing the breach.
Their collaboration with the FBI and other cybersecurity agencies is another point of contention.
A particularly contentious decision was Colonial Pipeline’s payment of a ransom to the attackers.
Yes, this move, while expedited service resumption, plunged the company into a complex ethical dilemma.
Post-attack, the company’s hefty investment in cybersecurity infrastructure and the implementation of stricter security protocols is noteworthy.
This reactive measure, while necessary, underscores a critical oversight in preemptive security strategies.
As 2024 rolls around today, we face new and evolving challenges. Now more than ever, we’re challenged to deploy and improve our incident management processes.
This means business and IT departments must continually refine their strategies to quickly address and resolve incidents.
By doing so, we can not only ensure smooth operations, but also adapt and grow in the face of ever-evolving challenges.
And certainly, this commitment to robust incident management is key to navigating the complexities of the modern business landscape.